DNS Tunnelling Linux Botnet
A new backdoor has been observed targeting Linux systems with the goal of machine escalation where malicious actors are enrolling machines into a botnet and acting as a conduit for downloading and installing rootkits. Qihoo 360’s Netlab security team called it B1tor20 based on its propagation using the file name ‘b1t,’ the XOR encryption algorithm, and the RC4 algorithm key length of 20 bytes.”
First observed propagating through the Log4J Vulnerability on February 9, 2022, the malware leverages a technique called DNS tunneling to build communication channels with command-and-control (C2) servers by encoding data in DNS queries and responses. Chaining Log4J and Linux Netfilter (CVE-2022-25636) malicious actors can easily esclate privileges and automate the attack. As these threats continue to increase its more important than ever to utilize a defense in depth approach with IPS next generation firewall guarding your internet edge.
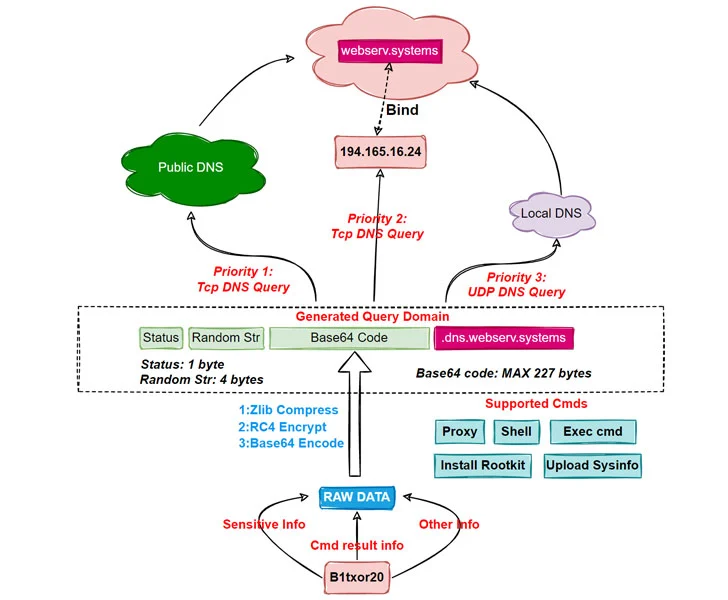
Once a machine is successfully compromised, the malware utilizes the DNS tunnel to retrieve and execute commands sent by the server.
“Bot sends the stolen sensitive information, command execution results, and any other information that needs to be delivered, after hiding it using specific encoding techniques, to C2 as a DNS request,” the researchers elaborated.
“After receiving the request, C2 sends the payload to the Bot side as a response to the DNS request. In this way, Bot and C2 achieve communication with the help of DNS protocol.”
A total of 15 commands are implemented, chief among them being uploading system information, executing arbitrary system commands, reading and writing files, starting and stopping proxy services, and creating reverse shells.
