Perimeter Security and Threat Model
Feature Article
CISA recently posted an article regarding Cyber actors routinely exploiting poor security configurations (either misconfigured or left unsecured), weak controls, and other poor cyber hygiene practices to gain initial access or as part of other tactics to compromise a victim’s system. The views here expressed don’t represent my enterprise role however I can state that patch management, asset inventories and defence-in-depth are three core abilities of an effective cyber security framework and often are overlooked. For example, Malicious actors commonly use the following techniques to gain initial access to victim networks.[TA0001]
- Exploit Public-Facing Application [T1190]
- External Remote Services [T1133]
- Phishing [T1566]
- Trusted Relationship [T1199]
- Valid Accounts [T1078]
All Network architects and Infrastructure System administrators should already understand Defence in-depth as a core methodology. I will define Defence in-depth as multiple security controls to protect a given asset. True zero trust architecture should accommodate multiple layers of security to protect a given asset.
As CISOs we should maintain perimeter assets inventory and map each security control utilized to protect these assets. This simple exercise can be very effective when understanding risk and risk mitigation. Let’s go ahead and start to unpackage an effective and classic perimeter security approach based on services typically exposed to the internet.
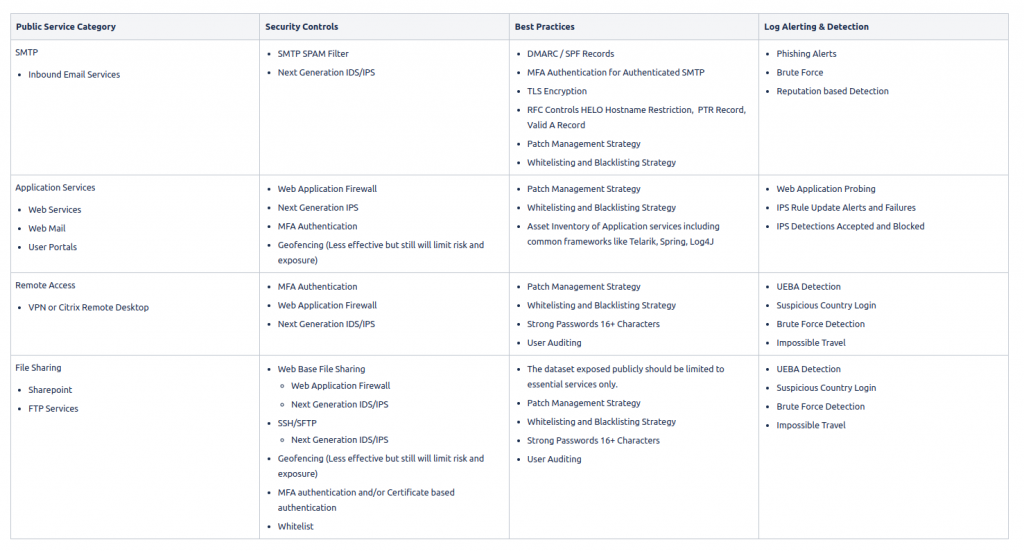
Best Practices
Following best practices, we should consider the following
- MFA for all public authentication
- No excuses we are managing an enterprise-grade security program as CISO
- IPS and Web Application in Blocking mode
- Easy to implement a non-blocking mode but also provides no risk mitigation.
- IPS provides real-time blocking and remediation.
- Management interfaces
- Whitelisted only and MFA Authentication
- Having a backdoor can be critical during incidents or hardware failures.
- Limit and validate access is only permitted to a small user group.
- Firewalls
- Inbound Default Deny for Network, Workstations and Servers
- Inventory
- Keep an active inventory of patches, versions, vendors, services
- Patch Management Strategy
- Patch regularly, frequently and understand the process end-to-end
- No excuses, too often we hear service availability is considered a risk, this essentially means you have never tested your DR plan. This is a very fair statement since patch regularly issues do arise, however proper testing of DR planning and live testing, migration testing, and architecture reviews can drive efficiency for patch management.
Validation
The most important is VALIDATION. we should always be validating our external security using multiple layers of depth!!!
- Active External scanning services
- Tenable or Qualisys.
- Red Team Threat vulnerability assessments
- Threat Risk assessment
- Penetration Testing
- Red Team
- Purple Team
Did you action the results of your last pentest, where the results were trusted and verified? Consider the following items as the Validation process for remediating findings.
Validation Process
- Findings Report
- Mitigate
- Validate Mitigation with rescanning
- Review report and repeat
Lastly consider whitelisting red team exercises and vulnerability scanners, since your IPS blocks these events this can give a false sense of security. I have seen companies set up an external scanning service and have IPS blocking these events to achieve clean reports.
As CISO my goal is to understand the real risk of services by performing risk sampling at multiple layers. For example, you can run monthly or quarterly scans to validate your intrusion protection system. However, a proper monitoring and SOC team should also pick up on the negative where IDS or Alerting is enabled. The common theme in the article is we have many layers of each control from validation to implementation and we have taken security-first approach to protect our organization.
